Lessons on Authority from Killing User Processes
This is a post I had sitting in draft form for a long while. Looking back, I’m less convinced my end solution is foolproof. But the research was interesting and I’d rather throw it out there.
I was working in an environment a while ago where I needed to terminate all processes in a user account, but with only tools built into Windows. Seemed easy enough, taskkill with a filter can accomplish that:
taskkill.exe /F /FI "USERNAME eq %USERNAME%"
I was running as SYSTEM, though, so I first had to parse out logged on users. While I was working on that a different approach was posed - filtering via exclusion.
taskkill.exe /F /FI "USERNAME ne NT AUTHORITY\*"
This was interesting. If you’ve ever looked at what accounts processes are running in you probably caught a pattern. Built-in Windows accounts like System, Local Service, and Network Service sit under NT AUTHORITY\<username>, but local user accounts show as %COMPUTERNAME%\<username>. If you’re joined to a domain, domain accounts show as %USERDOMAIN%\<username>. For example, here’s a Lenovo idea-PC with a local user account ‘ASDF’:
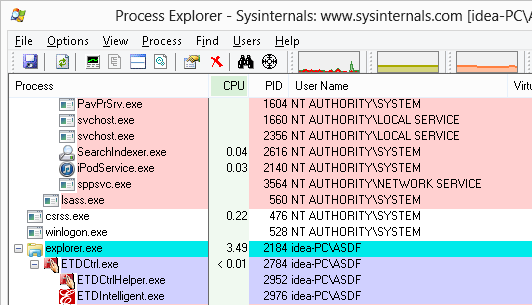
In an effort to terminate all user processes, then, taskkilling everything not NT AUTHORITY\* would successfully take out anything idea-PC\ASDF, or MyDomain\Joe or otherwise.
But it raised a question I didn’t know the answer to. Does Windows just have NT AUTHORITY, %USERDOMAIN% and %COMPUTERNAME%? What was the mechanism at work here? I wanted to find out.
DOMAINS AND AUTHORITIES
I went looking for information on the built-in accounts and landed at KB243330, Well-known security identifiers in Windows operating systems. The KB lists a metric ton of user accounts, groups, and other objects that are built-in to Windows. Each object has it’s own unique Security Identifier (SID). Among the list was NT Authority, defined as an identifier authority.
There is a noticable relationship between NT Authority’s SID and the SIDs of accounts under it:
S-1-5 NT Authority
S-1-5-18 NT Authority\SYSTEM
S-1-5-19 NT Authority\Local Service
S-1-5-20 NT Authority\Network Service
So I found TechNet’s Security Identifier Structure article to break down the SID format:
S-R-X-Y¹-Y²-Yⁿ-A
S indicates that the string is a SID.
R is the revision level.
X is the identifier authority value.
Y is a series of subauthority values
A is the account under the authorit[y][ies]
[...]
The most important information in a SID is contained in a series of one or more subauthority values. All values up to but not including the last value in the series collectively identify a domain in an enterprise. This part of the series is the domain identifier . The last value in the series identifies a particular account or group relative to a domain.
Perfect. In the case of SYSTEM, Local Service, and Network service, the last value in the SID string represents the account. That leaves 5 representing the domain, thus, the domain is NT Authority.
What about idea-PC\ASDF? The SID for the ASDF acount on the Lenovo is:
S-1-5-21-443461471-642785168-2980392841-1002
Then, 1002 represents ASDF. 5-21-443461471-642785168-2980392841 must represent idea-PC. This can be tested with the tool sid2user, which translates an SID to its friendly name:
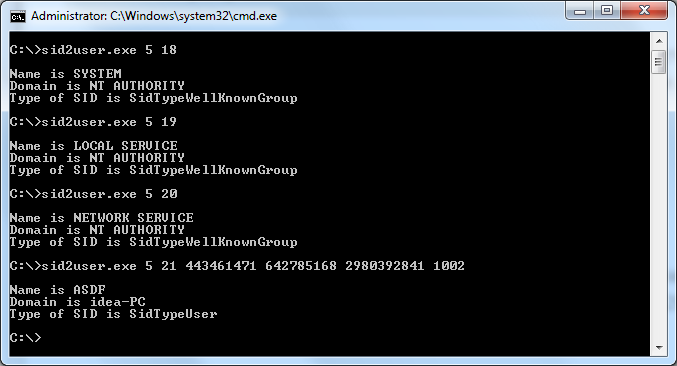
(By the by, for background on how this SID was generated by Windows, check out this MSDN article. The short version is that the local computer account and any enterprise domains will be under S-1-5-21-* with a three-block-wide randomly generated 96-bit number.)
Sid2user lines up perfectly and even helpfully lists the SID type as SIDTypeDomain for the idea-PC string.
Hunting for Hidden Domains
So what other domains are there? I pulled each unique authority/subauthority string from the KB article to check against sid2user. Just these four are of type SIDTypeDomain:
S-1-5 NT Psuedo Domain (NT Authority)
S-1-5-32 BUILTIN
S-1-5-80 NT SERVICE
S-1-16 Mandatory Label
From such a long list of SIDs I’m surprised there were only three domains. But hey, three new faces! In looking for documentation on them I found many other MSDN articles with SIDs not in the original KB article. There didn’t seem to be any easily understood database anywhere in documentation or in Windows, so I ended up rolling through some FOR loops. By incrementing authority and subauthority values and checking against sid2user, I found a bigger list:
S-1-5 NT Psuedo Domain (NT Authority)
S-1-5-32 BUILTIN
S-1-5-80 NT SERVICE
S-5-82 IIS APPPOOL
S-1-5-87 NT TASK
S-1-7 Internet$
S-1-16 Mandatory Label
S-1-5-90 Window Manager (Windows 8+)
Very interesting! Way beyond just NT Authority, but what do any of these do? Some were easier to find documentation on than others.
- BUILTIN contains a lot of default Windows groups like Administrators and Users. I wasn’t able to find an actual user account under the BUILTIN domain, just groups.
- NT SERVICE contains user accounts used by services such as Microsoft’s SQL Server service and TrustedInstaller.
- IIS Apppool, documented here, is fascinating! It only exists on machines with IIS installed indicating it’s possible to create new subauthorities at will! I spent some time investigating how this was done but wasn’t able to nail down the mechanism. But iissetup.exe and samcli.dll were involved.
- NT TASK appears to have been used by older scheduled tasks on Windows.
- Internet$ appears to be used with LSA authentication mechanisms but I couldn’t find any particularly good documentation. That is, except for this KB article that indicates Internet$ could be renamed to Authority$. Fun.
- Mandatory Label looks to be a result of how integrity labels were implemented Vista+.
- Window Manager holds user accounts for running the DWM.exe process on Windows 8+, it seems as a result of changes that made DWM not removable.
Applying the knowledge
For the taskkill filter, NT SERVICE, IIS Apppool, NT Task, and Window Manager could be confirmed as having user accounts running processes that would thus need to be filtered out. I don’t particularly care for the method given new subauthorites of any name can be generated, though.
But, I can still apply what I learned to find a solution. Perhaps instead of blacklisting with ne or trying to parse usernames, I could just focus on the domains users I care about appear under - anything S-1-5-21-*. Taskkill unfortunately doesn’t support filtering with SID strings, but perhaps some environment variables can do the trick:
taskkill.exe /F /FI "USERNAME eq %COMPUTERNAME%\*" /FI "USERNAME eq %USERDOMAIN%\*"